Domains is a group of computers and other resources that are part of a network and share a common directory database .Once a server has been installed, you can use the Active Directory Wizard to install Active Directory in order to install Active directory on the first server on the network, that server must have the access to a server running DNS (Domain Name Service). If you don't have install this service on your server then you will have to install this service during the Active Directory installation the 'domain' is simply your computer address not to confused with an URL. A domain address might look something like 211.170.469. A Domain is simply a name with which we use to refer a computer. It mean online property!
The domain is the "end part" of the Uniform Resource Locator (URL) of an Internet address. It identifies a subdivision of the net so that the location of an individual, group or organization can be pinpointed. Domains include: .com, .net, .gov, .edu, .mil, .uk, .fr and a whole bunch more.
Other meanings Domain has more than one meaning. It can mean a place under one rule or one control, or it can mean a sphere of influence or control. In mathematics, it means the set of possible values of an independent variable. In physics, it means a discreet region of magnetism in ferromagnetic material. Finally, if you add an e at the end to make the word Domain, then it means a vineyard.
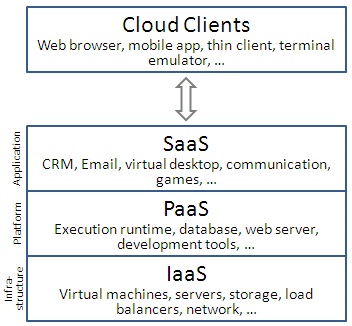
1. Cloud Computing:
Definition
Cloud computing is a recently evolved computing terminology or metaphor based on utility and consumption of computing resources. Cloud computing involves deploying groups of remote servers and software networks that allow centralized data storage and online access to computer services or resources. Clouds can be classified as public, private or hybrid.
Introduction:
Deployment models
-
Private cloud
-
Public cloud
-
Hybrid cloud
Others
-
Community cloud
-
Distributed cloud
-
Intercloud
-
Multicloud
Service models
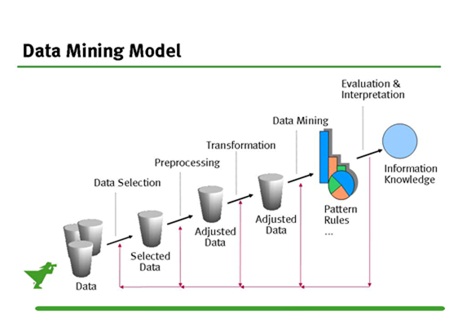
2. Data Mining:
Definition
Data mining (sometimes called data or knowledge discovery) is the process of analyzing data from different perspectives and summarizing it into useful information - information that can be used to increase revenue, cuts costs, or both. Data mining software is one of a number of analytical tools for analyzing data. It allows users to analyze data from many different dimensions or angles, categorize it, and summarize the relationships identified. Technically, data mining is the process of finding correlations or patterns among dozens of fields in large relational databases.
Introduction:
BLOCK DIAGRAM:
Data, Information, and Knowledge
Data
Data are any facts, numbers, or text that can be processed by a computer. Today, organizations are accumulating vast and growing amounts of data in different formats and different databases. This includes:
-
operational or transactional data such as, sales, cost, inventory, payroll, and accounting
-
nonoperational data, such as industry sales, forecast data, and macro-economic data
-
meta data - data about the data itself, such as logical database design or data dictionary definitions
Information
The patterns, associations, or relationships among all this data can provide information. For example, analysis of retail point of sale transaction data can yield information on which products are selling and when.
Knowledge
Information can be converted into knowledge about historical patterns and future trends. For example, summary information on retail supermarket sales can be analyzed in light of promotional efforts to provide knowledge of consumer buying behavior. Thus, a manufacturer or retailer could determine which items are most susceptible to promotional efforts.
Data Warehouses
Dramatic advances in data capture, processing power, data transmission, and storage capabilities are enabling organizations to integrate their various databases into data warehouses. Data warehousing is defined as a process of centralized data management and retrieval. Data warehousing, like data mining, is a relatively new term although the concept itself has been around for years. Data warehousing represents an ideal vision of maintaining a central repository of all organizational data. Centralization of data is needed to maximize user access and analysis. Dramatic technological advances are making this vision a reality for many companies. And, equally dramatic advances in data analysis software are allowing users to access this data freely. The data analysis software is what supports data mining.
3. Database security
Database security
concerns the use of a broad range of information security controls to protect databases (potentially including the data, the database applications or stored functions, the database systems, the database servers and the associated network links) against compromises of their confidentiality, integrity and availability.
INTRODUCTION:
Many layers and types of information security control are appropriate to databases, including:
-
Access control
-
Auditing
-
Authentication
-
Encryption
-
Integrity controls
-
Encryption
-
Application security
-
Database Security applying Statistical Method
Databases have been largely secured against hackers through network security measures such as firewalls, and network-based intrusion detection systems. While network security controls remain valuable in this regard, securing the database systems themselves, and the programs/functions and data within them, has arguably become more critical as networks are increasingly opened to wider access, in particular access from the Internet. Furthermore, system, program, function and data access controls, along with the associated user identification, authentication and rights management functions, have always been important to limit and in some cases log the activities of authorized users and administrators. In other words, these are complementary approaches to database security, working from both the outside-in and the inside-out as it were.
Many organizations develop their own "baseline" security standards and designs detailing basic security control measures for their database systems. These may reflect general information security requirements or obligations imposed by corporate information security policies and applicable laws and regulations (e.g. concerning privacy, financial management and reporting systems), along with generally accepted good database security practices (such as appropriate hardening of the underlying systems) and perhaps security recommendations from the relevant database system and software vendors.
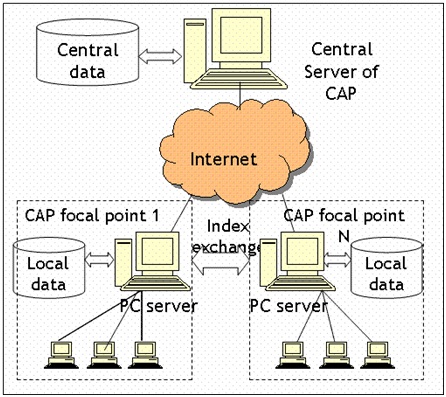
4. Distributed Networking
Definition
A distributed network is a type of computer network that is spread over different networks. This provides a single data communication network, which can be managed jointly or separately by each network. Besides shared communication within the network, a distributed network often also distributes processing.
INTRODUCTION:
Distributed Network
Distributed networks are part of distributed computing architecture, in which enterprise IT infrastructure resources are divided over a number of networks, processors and intermediary devices. A distributed network is powered by network management software, which manages and monitors data routing, combining and allocating network bandwidth, access control and other core networking processes.
BLOCK DIAGRAM:
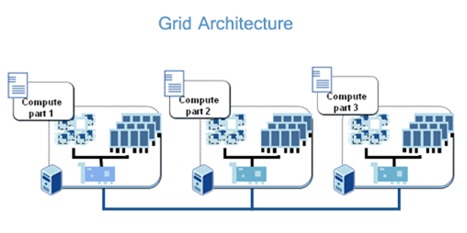
5. Grid Computing:
Definition
Grid computing (or the use of a computational grid) is applying the resources of many computers in a network to a single problem at the same time - usually to a scientific or technical problem that requires a great number of computer processing cycles or access to large amounts of data.
INTRODUCTION:
Grid computing requires the use of software that can divide and farm out pieces of a program to as many as several thousand computers. Grid computing can be thought of as distributed and large-scale cluster computing and as a form of network-distributed parallel processing. It can be confined to the network of computer workstations within a corporation or it can be a public collaboration (in which case it is also sometimes known as a form of peer-to-peer computing).
A number of corporations, professional groups, university consortiums, and other groups have developed or are developing frameworks and software for managing grid computing projects. The European Community (EU) is sponsoring a project for a grid for high-energy physics, earth observation, and biology applications. In the United States, the National Technology Grid is prototyping a computational grid for infrastructure and an access grid for people. Sun Microsystems offers Grid Engine software. Described as a distributed resource management (DRM) tool, Grid Engine allows engineers at companies like Sony and Synopsys to pool the computer cycles on up to 80 workstations at a time. (At this scale, grid computing can be seen as a more extreme case of load balancing.)
ARCTECTURE:
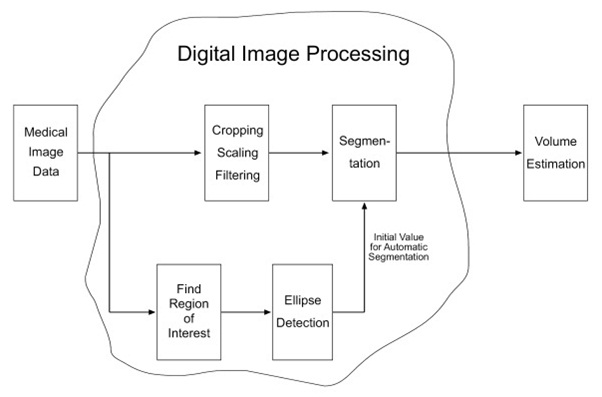
6. IMAGE PROCESSING
Definition
Image processing is any form of signal processing for which the input is an image, such as a photograph or video frame; the output of image processing may be either an image or a set of characteristics or parameters related to the image. Most image-processing techniques involve treating the image as a two-dimensionalsignal and applying standard signal-processing techniques to it.
INTRODUCTION:
Image processing usually refers to digital image processing, but optical and analog image processing also are possible. This article is about general techniques that apply to all of them. The acquisition of images (producing the input image in the first place) is referred to as imaging.
Closely related to image processing are computer graphics and computer vision. In computer graphics, images are manually made from physical models of objects, environments, and lighting, instead of being acquired (via imaging devices such as cameras) from natural scenes, as in most animated movies. Computer vision, on the other hand, is often considered high-level image processing out of which a machine/computer/software intends to decipher the physical contents of an image or a sequence of images (e.g., videos or 3D full-body magnetic resonance scans).
In modern sciences and technologies, images also gain much broader scopes due to the ever growing importance of scientific visualization (of often large-scale complex scientific/experimental data). Examples include microarray data in genetic research, or real-time multi-asset portfolio trading in finance.
BLOCK DIAGRAM:
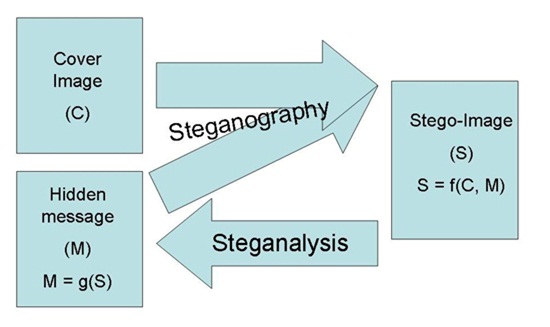
7. Information Security
Definition
Information security, sometimes shortened to InfoSec, is the practice of defending information from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. It is a general term that can be used regardless of the form the data may take.
INTRODUCTION:
IT securitySometimes referred to as computer security, Information Technology security is information security applied to technology (most often some form of computer system). It is worthwhile to note that a computer does not necessarily mean a home desktop. A computer is any device with a processor and some memory. Such devices can range from non-networked standalone devices as simple as calculators, to networked mobile computing devices such as smartphones and tablet computers. IT security specialists are almost always found in any major enterprise/establishment due to the nature and value of the data within larger businesses. They are responsible for keeping all of the technology within the company secure from malicious cyber attacks that often attempt to breach into critical private information or gain control of the internal systems.
Information assuranceThe act of ensuring that data is not lost when critical issues arise. These issues include but are not limited to: natural disasters, computer/server malfunction, physical theft, or any other instance where data has the potential of being lost. Since most information is stored on computers in our modern era, information assurance is typically dealt with by IT security specialists. One of the most common methods of providing information assurance is to have an off-site backup of the data in case one of the mentioned issues arise..
ThreatsComputer system threats come in many different forms. Some of the most common threats today are software attacks, theft of intellectual property, identity theft, theft of equipment or information, sabotage, and information extortion. Most people have experienced software attacks of some sort. Viruses, worms, phishing attacks, and trojan horses are a few common examples of software attacks..
BLOCK DIAGRAM:
8. Mobile Computing:
Definition
Mobile Computing is "taking a computer and all necessary files and software out into the field". Mobile computing is any type of computing which use Internet or intranet and respective communications links, as WAN, LAN, WLAN etc. Mobile computers may form a wireless personal network or a piconet.
INTRODUCTION:
DATA COMMUNICATIONS
Data Communications is the exchange of data using existing communication networks. The term data covers a wide range of applications including File Transfer (FT), interconnection between Wide-Area-Networks (WAN), facsimile (fax), electronic mail, access to the internet and the World Wide Web (WWW).
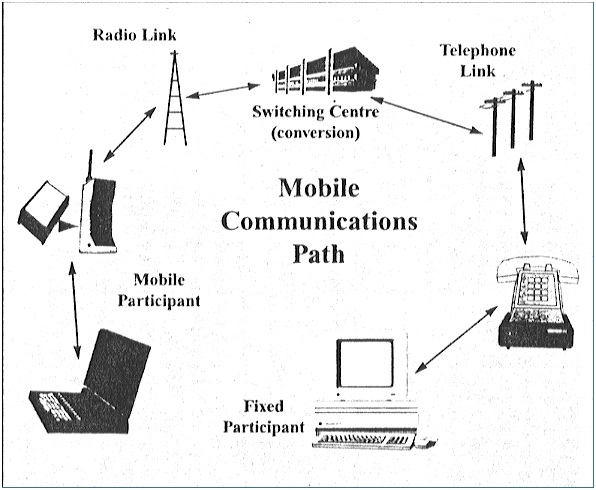
Mobile Communications Overview
Data Communications have been achieved using a variety of networks such as PSTN, leased-lines and more recently ISDN (Integrated Services Data Network) and ATM (Asynchronous Transfer Mode)/Frame Relay. These networks are partly or totally analogue or digital using technologies such as circuit - switching, packet - switching e.t.c.
9. NETWORK:
Definition
A network is a group of two or more computer systems linked together. There are many types of computer networks, including: local-area networks (LANs) : The computers are geographically close together (that is, in the same building).
INTRODUCTION:
Network computer devices that originate, route and terminate the data are called network nodes.[1] Nodes can include hosts such as personal computers, phones, servers as well as networking hardware. Two such devices are said to be networked together when one device is able to exchange information with the other device, whether or not they have a direct connection to each other.
Computer networks differ in the transmission media used to carry their signals, the communications protocols to organize network traffic, the network's size, topology and organizational intent. In most cases, communications protocols are layered on (i.e. work using) other more specific or more general communications protocols, except for the physical layer that directly deals with the transmission media.
Computer networks support applications such as access to the World Wide Web, shared use of application and storage servers, printers, and fax machines, and use of email and instant messaging applications.
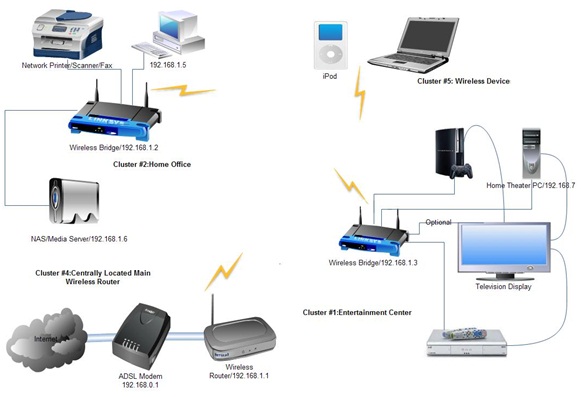
10. NETWORK SECURITY:
Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources.
INTRODUCTION:
Network security starts with authenticating, commonly with a username and a password. Since this requires just one detail authenticating the user name —i.e. the password— this is sometimes termed one-factor authentication. With two-factor authentication, something the user 'has' is also used (e.g. a security token or 'dongle', an ATM card, or a mobile phone); and with three-factor authentication, something the user 'is' is also used (e.g. a fingerprint or retinal scan).
Once authenticated, a firewall enforces access policies such as what services are allowed to be accessed by the network users.[2] Though effective to prevent unauthorized access, this component may fail to check potentially harmful content such as computer worms or Trojans being transmitted over the network. Anti-virus software or an intrusion prevention system (IPS)[3] help detect and inhibit the action of such malware. An anomaly-based intrusion detection system may also monitor the network like wireshark traffic and may be logged for audit purposes and for later high-level analysis.
Project Diagram:
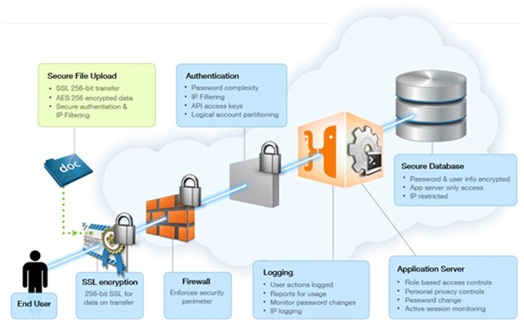
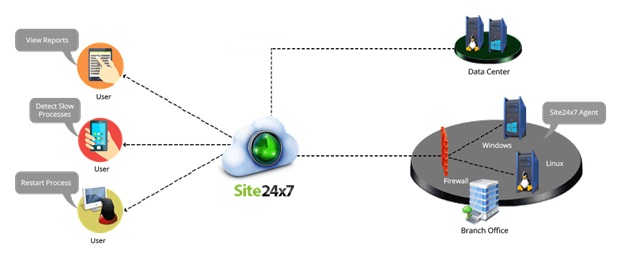
11. Server Performance:
Monitoring a server isn't something you should do haphazardly. You need to have a clear plan—a set of goals that you hope to achieve. Let's take a look at the reasons you may want to monitor a server and at the tools you can use to do this.
INTRODUCTION:
Why Monitor Your Server?
Troubleshooting server performance problems is a key reason for monitoring. For example, users may be having problems connecting to the server and you may want to monitor the server to troubleshoot these problems. Here, your goal would be to track down the problem using the available monitoring resources and then to resolve it.
Another common reason for wanting to monitor a server is to improve server performance. You do this by improving disk I/O, reducing CPU usage, and cutting down on the network traffic load on the server. Unfortunately, there are often trade-offs to be made when it comes to resource usage. For example, as the number of users accessing a server grows, you may not be able to reduce the network traffic load, but you may be able to improve server performance through load balancing or by distributing key data files on separate drives.
Diagram: